1 User Roles
The following roles are available to users:
|
Role |
Description |
|---|---|
|
Risk Investigator |
Allows a user to review and take action on incidents, see entity and event details, and to search and filter events. This role is typically assigned to someone with a job title such as fraud agent, financial crime analyst or AML investigator. |
|
Risk Analyst |
Allows a user to manage incidents in the same way as a Risk Investigator, manage analytics in the same way as a Risk Analyst and approve changes to analytics made by a Risk Analyst another Risk Manager or their own changes. If you do not want a Risk Manager to have permissions to accept their own changes, please speak to your Account Manager. |
|
Risk Manager |
Allows a user to manage incidents in the same way as a Risk Analyst and approve changes to analytics made by a Risk Analyst. |
|
Administrator |
Grants a user all the permissions available to other user roles. In addition, this role allows a user to create other users, and manage the roles assigned to other users within your organisation. Note: This role is reserved for Thredd use. |
Thredd will set up the user roles for your organisation. You will be able to access the Fraud Transaction Monitoring Portal using Single Sign-On (SSO).
1.1 Creating a New User
If you need to create a new user, please raise a Thredd Customer Services Jira and provide details of the username, email address, user role (as above) and user contact mobile phone number.
Thredd will be set up users with Single Sign-On (SSO)![]() An identification method that enables users to log in to multiple applications and websites with one set of credentials. and the users will need to authenticate via their mobile device in order to access the Fraud Portal.
An identification method that enables users to log in to multiple applications and websites with one set of credentials. and the users will need to authenticate via their mobile device in order to access the Fraud Portal.
1.2 Viewing a User's Permissions
When a user logs in to the Fraud Transaction Monitoring Portal, their User Role and related permissions are displayed on the Portal Dashboard page. See the example below:
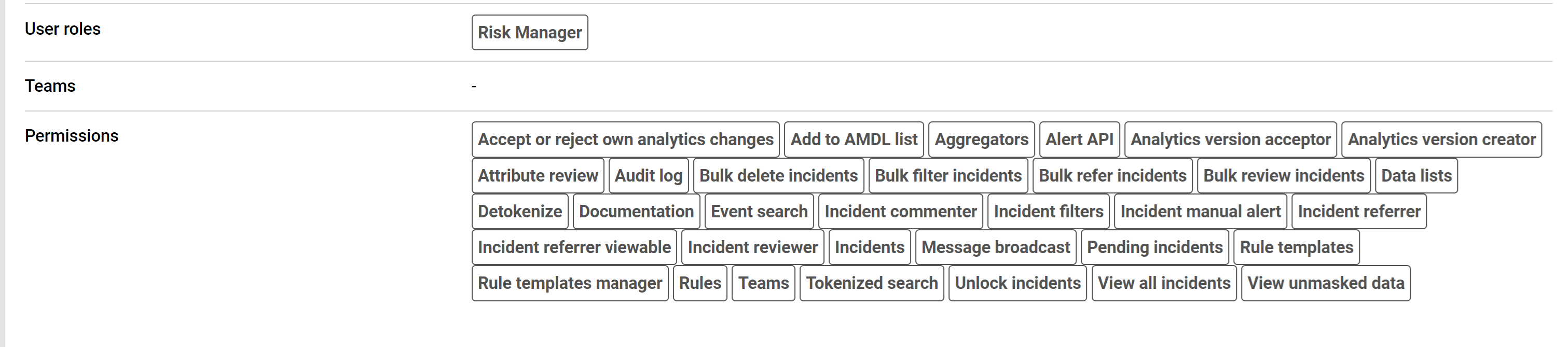
Figure 1: User roles and permissions shown on the Dashboard
1.3 List of User Permissions
The lists of permissions below show which permissions are assigned, by default, to each user role.
In the lists below, permissions that require another permission (referred to as the "parent permission") are indented below their parent permission, with a '∟' to indicate the parent-child relationship.